SOME CONTENTS OF INFORMATION SECURITY, ANTI-VIRUT, BASIC MACHINE PROTECTION
I. Object:
All new employees join the company.
II. Request:
Read and understand the entire content on the first day of work. If you don’t understand something, ask some people in the company to understand.
III. Documentation level:
- These are just the most basic mandatory knowledge and requirements to help employees not be infected with computer viruses, malicious software, be tricked into getting passwords, ..
- During the work process, there will be many other specific and unique situations, and at that time, please discuss with your superiors to handle them.
IV. Content
A) Basic definitions
1) Virus
These are pieces of malicious code, embedded in other files such as an executable file, a word file, an image file, etc.
- Viruses have the ability to replicate themselves, causing harm to that computer, and possibly other computers on the same LAN.
- The virus itself is not a separate, independent file, so it cannot be seen in any folder.
2) Worm, Trojan,… (malware in general):
These are independent files that exist on the computer and may or may not copy themselves. And in general, it is harmful to computers and can affect computers on the same LAN
3) Phising:
- It is a scam or enticement through emails or bad websites.
B) Performance requirements.
- Related to Viruses, Worms, Trojans, etc.
1) Do not download strange files from strange websites. Please check the website’s URL carefully before downloading.
2) Absolutely do not arbitrarily install strange software. Even familiar software (eg: Unikey.exe) must be downloaded from the official website (eg: Unikey.org) and not from anywhere else.
Before installing a certain file, the consent of the Leaders (currently Trieu, Luan, Nhan, Long) must be obtained.
3) The computer must have anti-virus software installed (refer to Human Resources for which software), and perform an Update of that anti-virus software (actually not updating the software, but updating the latest virus information for the computer). software) and scan (scan) on the first day of work.
4) Once a month, you must redo the work in Section 3, Part B above.
5) Once a month, the operating system (eg Windows) must be updated to the latest version to update patches.
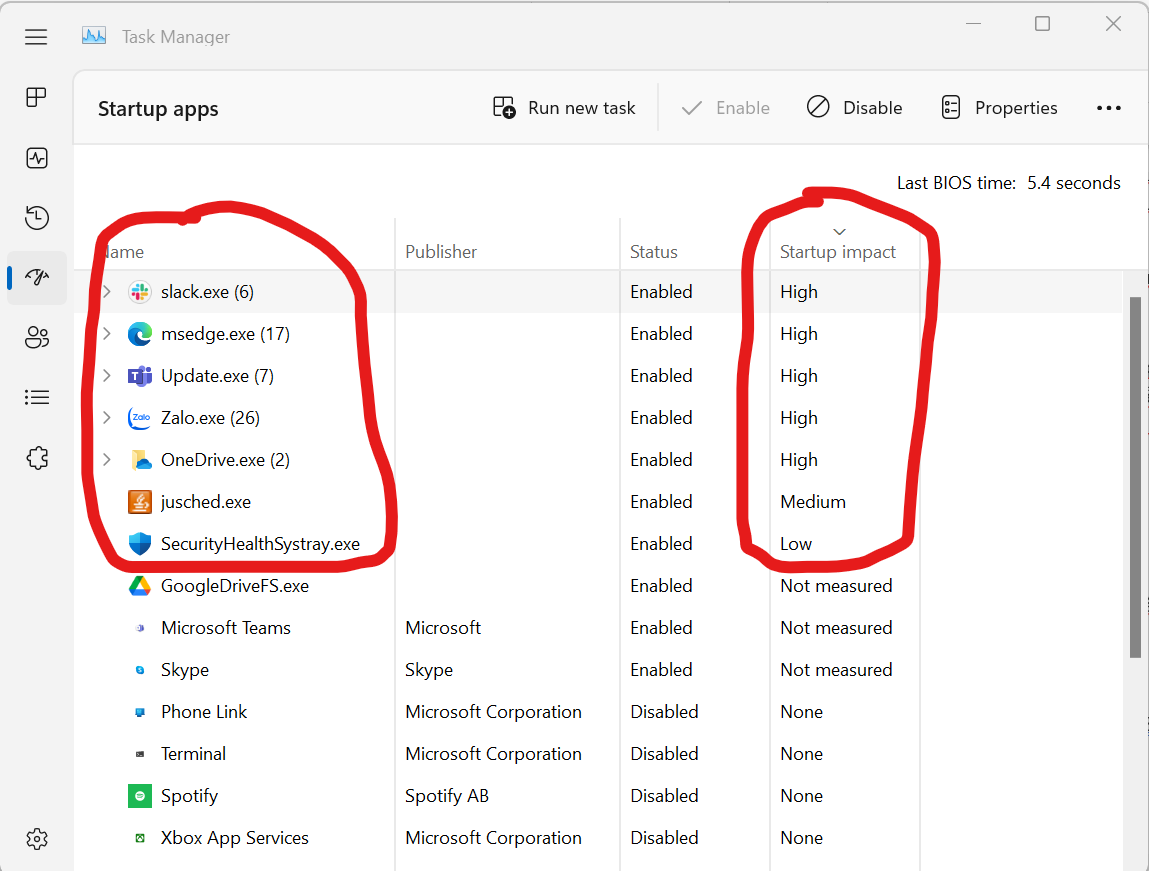
6) Once a month, open the task manager to see the software running at “Start up”. If you see anything strange, call the leaders immediately.
- Regarding email.
1) When you see an email coming in, double-check where it came from (see the name after the @ sign of the email). If you see a strange address, either delete it, or if you want to open it, ask the leader and then open it.
For example:

This email says it is from DHL, but the email name is “parcelfromchina.com” which is a completely unrelated name to DHL, so 100% this email is a scam email.
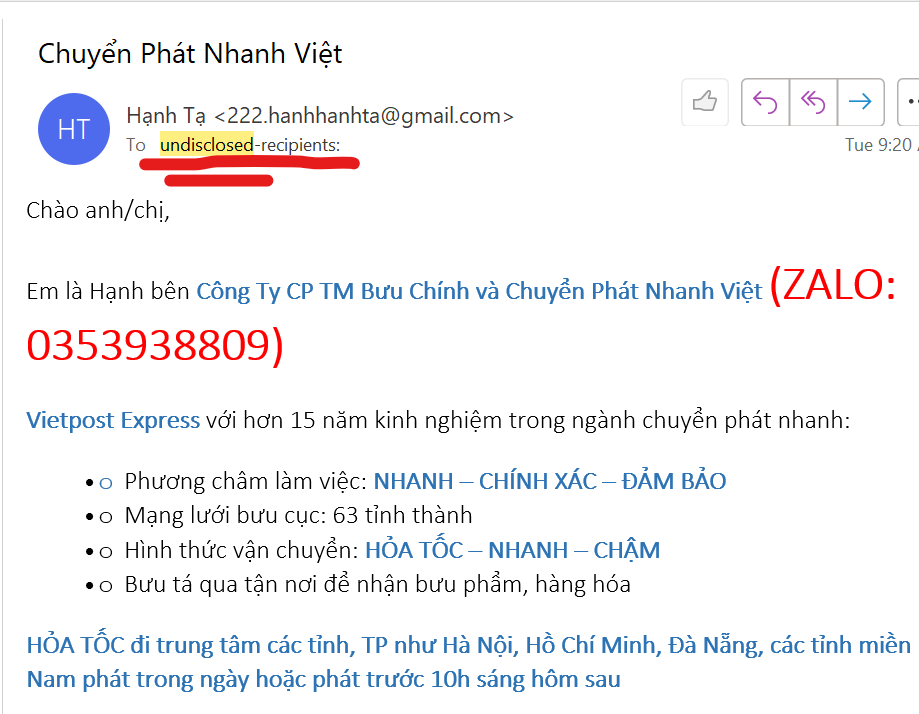
2) When an email is sent to you that is not sent directly to your email, but is sent to a group, with a recipient address of the type “undisclosed recipients”, that is also a scam.
3) When you send an email, double-check that the recipient’s email address is correct.
For example, I intend to send it to Yamato company, but the recipient’s email address is [email protected]
(there is a “.sg” part that is very suspicious) then stop sending immediately and report to Leaders(
4) When sending attachments, never send files ending in .exe or .com or .dll. Even compressing these filles into a compressed file named xxxxx.zip or xxxxxx.rar does not work. If you want to send, you must ask the leaders.
- Regarding Password types.
1) Absolutely do not provide your password or Secret Key to anyone else.
If required to provide, it must be approved by Leaders.
2) Passwords that employees set themselves must be sufficiently difficult. There are Chinese characters, numbers, and special characters !@#$, with a length greater than 9 characters.
Absolutely do not set a simple password like absy2533 because this password can be broken within 10 seconds.
3) Do not save malicious passwords on unprotected files.
It is recommended to save all passwords in a word file, and that word file is set with a password to open. Then you only need to remember 1 password for that word file. The code to open the word file must also be difficult enough as mentioned above.
4) Limit sending passwords via email or chat (Skype, zalo, …).
If you have to send it via chat, please confirm with the recipient so that once the recipient has saved the password, I will delete/recall the message containing the password.
The opposite is also the same. When someone sends you a password by text message, save that password, then ask the sender to delete/revoke that message.
5) When using a computer outside an internet shop or a computer borrowed from someone, you should ABSOLUTELY not save your password on that computer.
- Regarding file sharing, e.g. Google drive.
1) Minimize sharing a public file (anyone can open it). Please ask the account of the person who wants to share to share it with them, or send the google address of that file to the person who wants to see the request (request) and then go to accept/approve (allow access).
2) Get into the habit of right-clicking on a folder or file on Google to see who that file is currently being shared with. If you see a stranger, immediately remove that person’s access rights. Delete it now, then ask later if necessary, instead of asking before deleting.
3) Do not arbitrarily create your own Google Drive to save source code files or company documents. The company has its own Google drive, ask leaders to know which files should be saved where.
- Some other content.
- The last one
When you feel anything unsafe, strange, unusual, immediately talk to the leader.
Everyone please note: read the information carefully to comply with this announcement!